SSO setup with DUO
Setting up DUO with Kazoo
Requirements
To use DUO to log in to Kazoo, you will need the following components:
- DUO SSO subject matter expert or technical contact
- DUO Access Gateway with a configured authentication source
- A YouEarnedIt! subdomain
***Important Note:*** If users will be accessing mobile app, please ensure that configuration allows access to SSO connections outside of the company’s network.
Setup
Create a cloud app within Duo
- Log in to the Duo Admin Panel and click Applications on the left navigation, and then click Protect an Application.
- Alternately, you can choose the “Add New -> Application” on the right hand side of the Dashboard view.
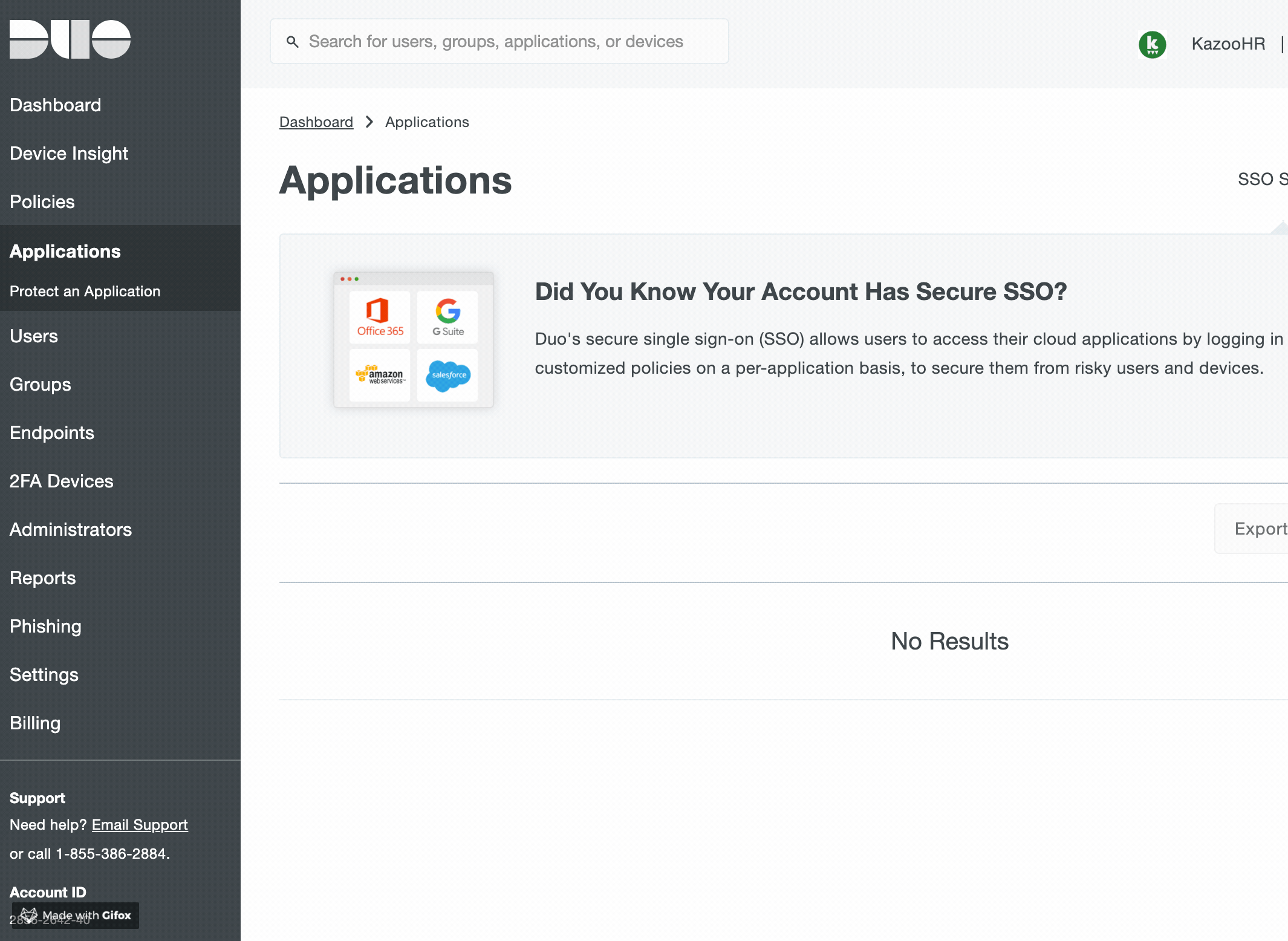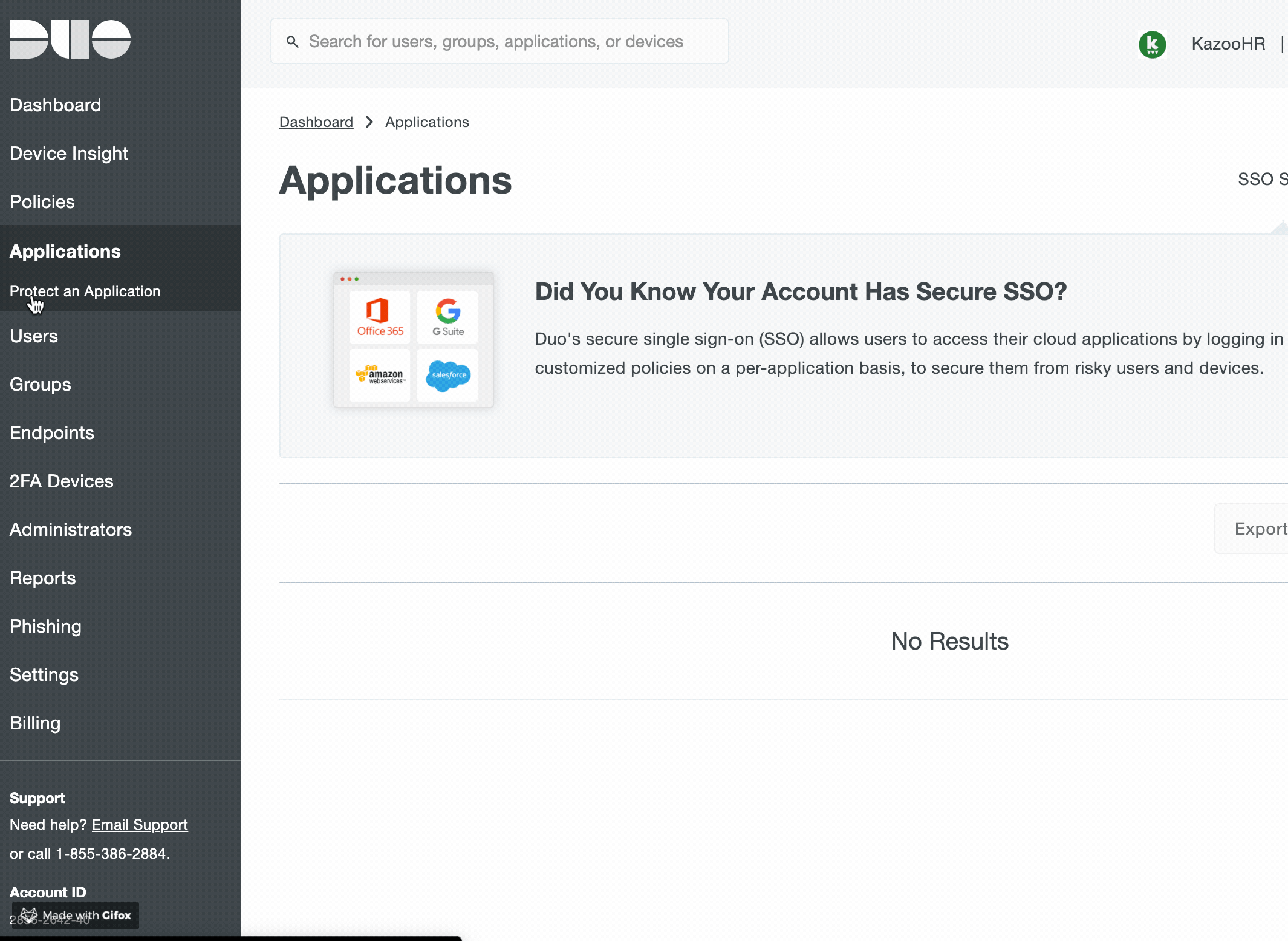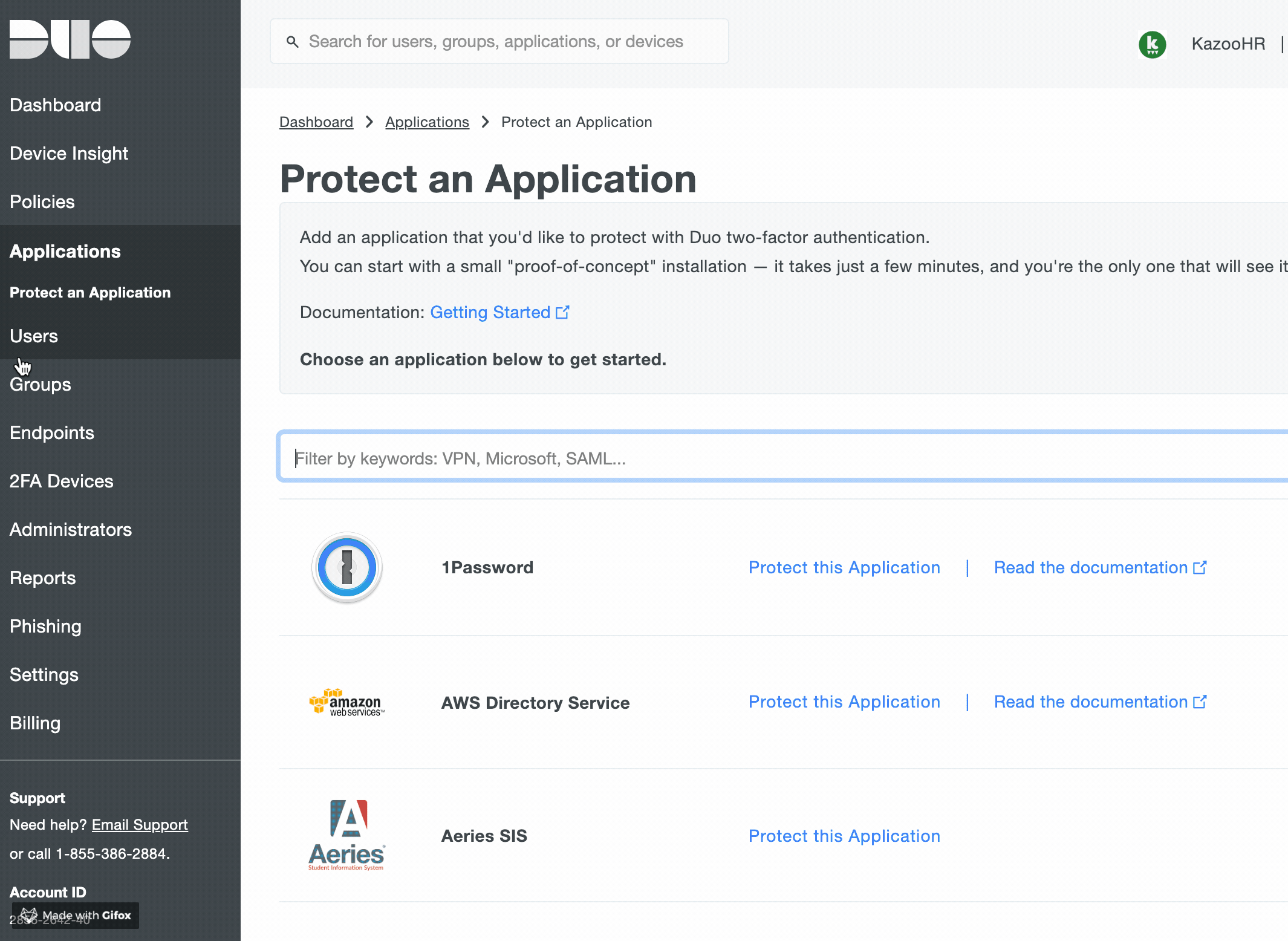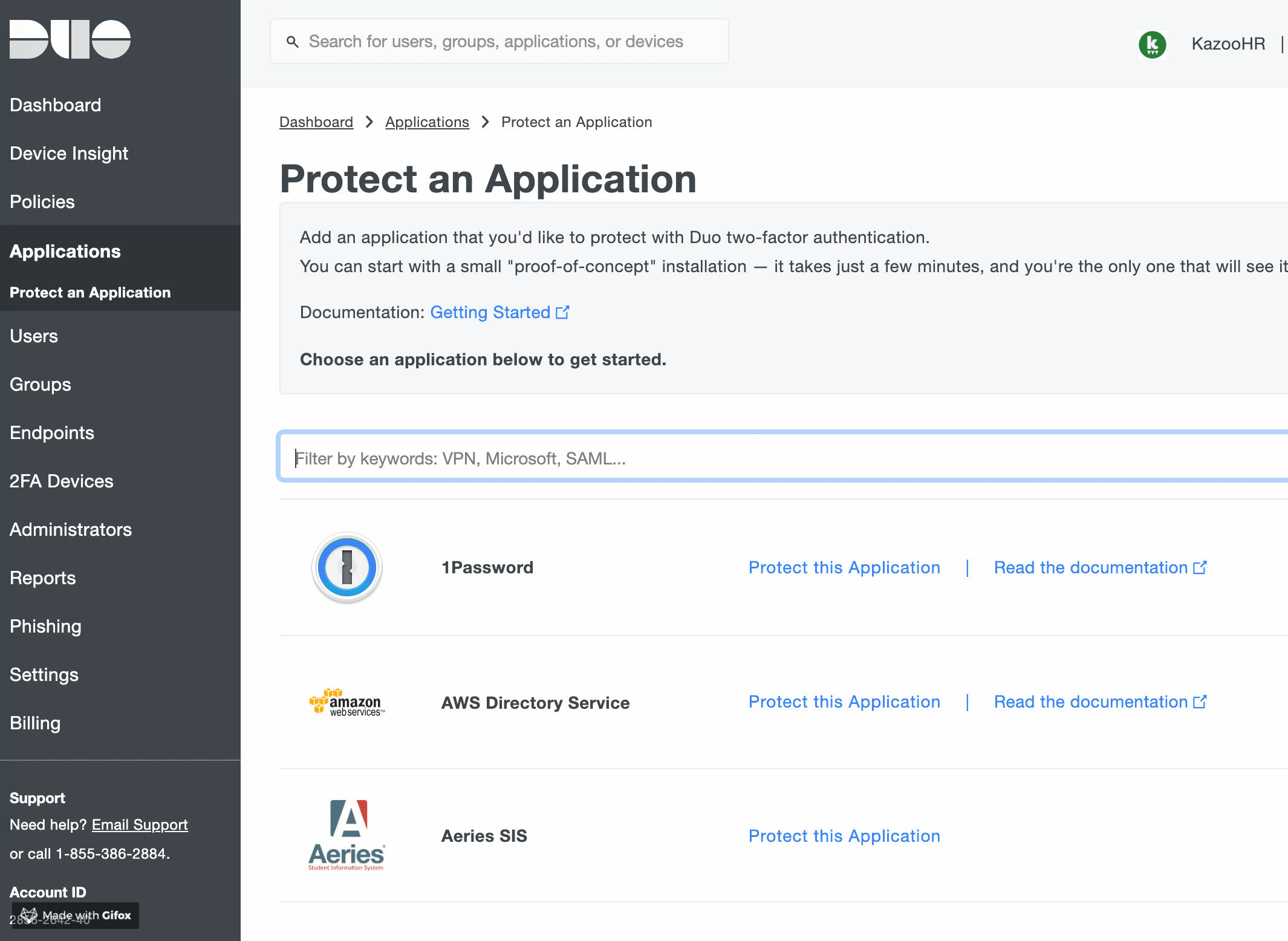
- Locate
SAML - Service Providerin the list of applications, and then click theProtect this Applicationlink.

You’ll be taken to a page that looks like this:
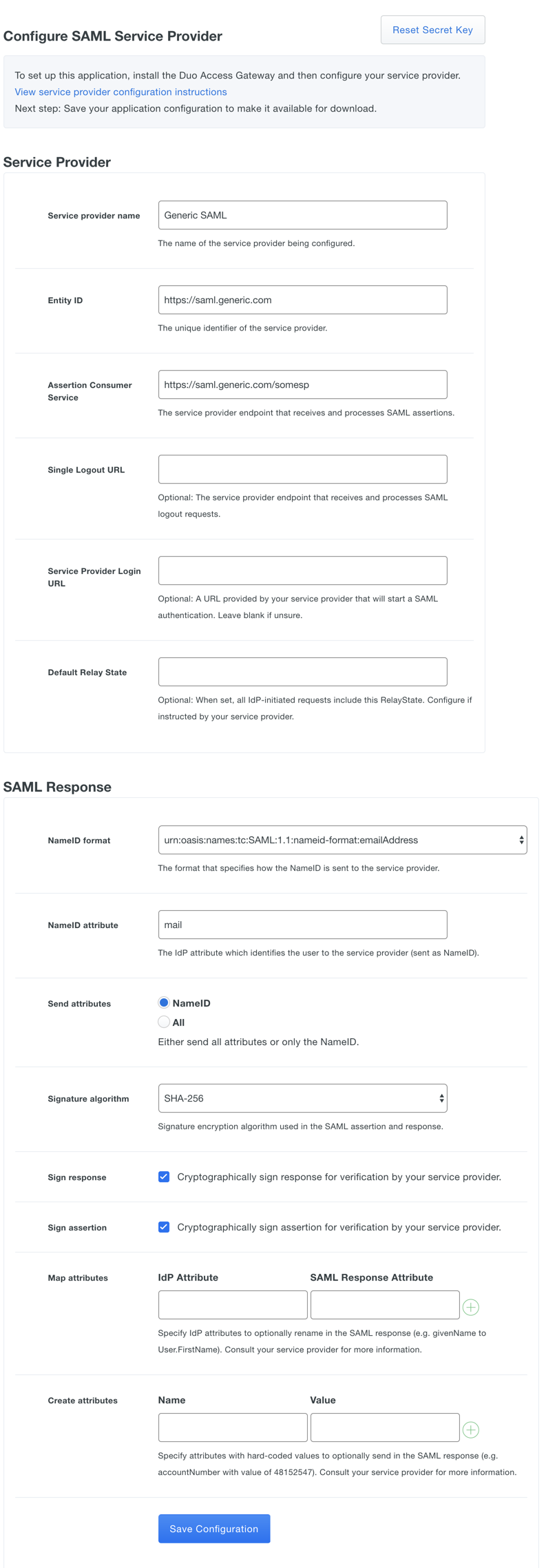
- Enter the following information about the app in the Service Provider section:
| Name | Description | Required/Optional | Example |
|---|---|---|---|
| Service Provider Name | The name of the service provider. | Required | KazooHR |
| Entity ID | The service provider identifier. | Required | (subdomain).youearnedit.com* |
| Assertion Consumer Service | The URL where your service provider receives SAML assertions. | Required | https://(subdomain).youearnedit.com/saml/acs* |
| Single Logout URL | The URL where your service provider receives SAML logout assertions. | Optional | |
| Service Provider Login URL | Enter the URL for IdP-initiated logins if your service provider specifies one. | Optional | |
| Default Relay State | If your service provider requires a specific RelayState parameter, enter it here. | Optional | |
* (subdomain) = assigned YEI subdomain |
- Complete the SAML Response section and click the Save Configuration button:
| Name | Description | Required / Optional |
|---|---|---|
| NameID format | Format of NameID when sent to the service provider. | Required |
| NameID attribute | The authentication source attribute used to identify the user to KazooHR. This attribute is sent as the NameID. This is often a user’s e-mail address (“mail” or “email”). See the list below for the names of common attributes from Duo Access Gateway authentication sources. | Required |
| Send attributes | By default Duo Access Gateway sends only the NameID IdP attribute to a service provider. Mapping or creating any additional attributes will also cause Duo Access Gateway to send all attributes. | Optional |
| Signature Algorithm | Defaults to SHA-256. Leave as SHA-256 | Required |
| Sign response | Leave this option enabled for the Duo Access Gateway to sign the SAML response. Uncheck the box if the response should not be signed. | Choice required |
| Sign assertion | Leave this option enabled for the DAG to sign the SAML assertion. Uncheck the box if the assertion should not be signed. | Choice required |
| Map attributes | If needed, specific names for the attributes sent by the DAG identity provider, you can map the authentication source attributes to the required names here. Enter the attribute name from your authentication source on the left, and the new attribute name on the right. See the list below for the names of common attributes. | Optional |
| Attribute | SAML IdP |
|---|---|
| mail or email | |
| Username | mail or email |
| First name | given_name |
| Last name | sn |
From here, DUO asks for specific authentication policies. These policies can be chosen from a list or created from the setup screen. Please consult your DUO subject matter expert or technical contact to ensure the correct policies are applied.
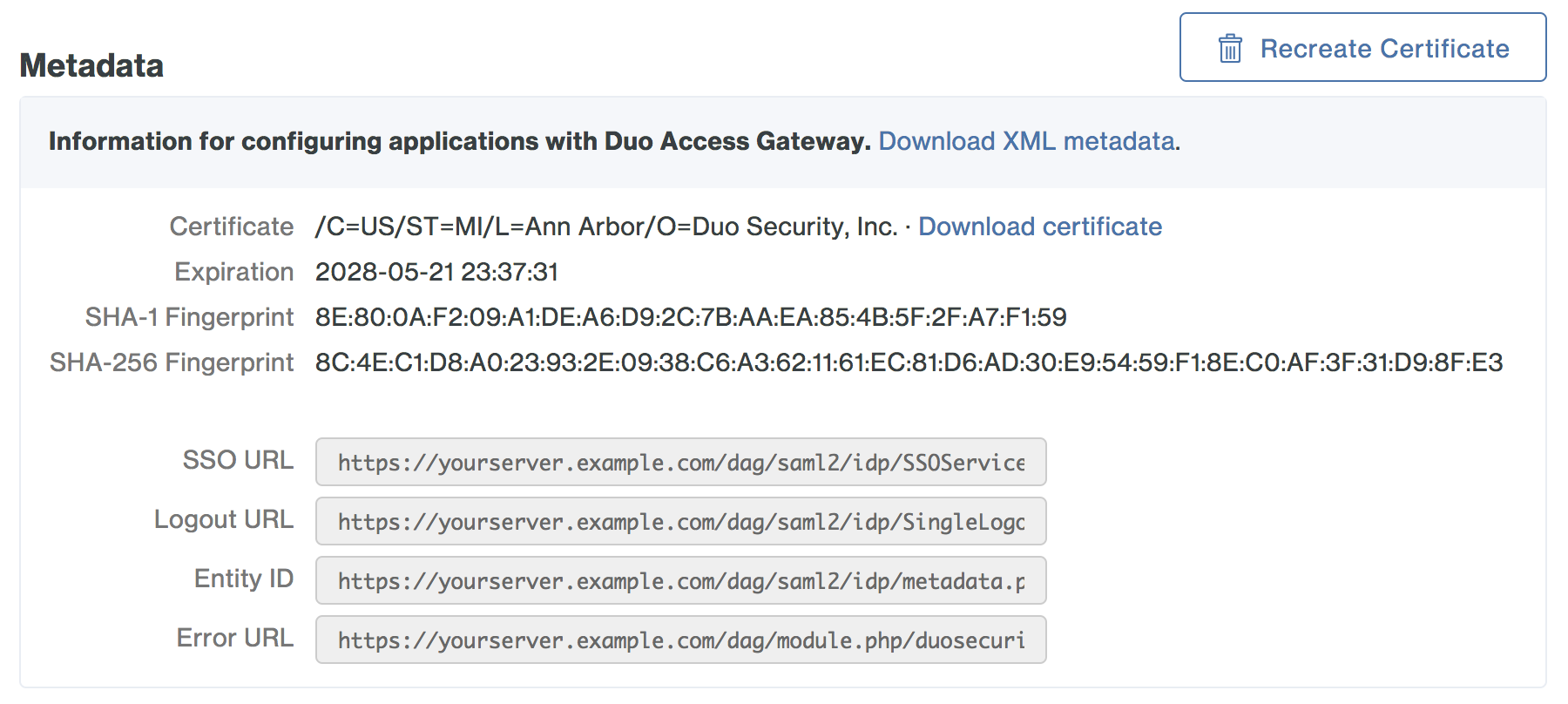
Once the above configuration has been completed, please follow the instructions given by DUO on how to add the application to your Duo Access Gateway found here.
Next the metadata for this application will need to be provided to the Customer Success Launch team member that is assigned to your company. Instructions on locating this information can be found here.